Decipher Network Traffic: eBPF for TCP/IP Header Examination
Understanding network traffic is crucial for troubleshooting, security analysis, and performance optimization. Traditional methods often involve intrusive tools that impact system performance or require specialized hardware. However, the extended Berkeley Packet Filter (eBPF) offers a revolutionary approach, allowing for efficient and low-overhead examination of network traffic, including deep dives into TCP/IP headers. This article explores how eBPF empowers you to decipher network traffic with unprecedented granularity.
What is eBPF and Why is it Relevant to Network Traffic Analysis?
eBPF is a powerful technology that allows you to run sandboxed programs within the Linux kernel without requiring module loading or kernel recompilation. This means you can analyze network traffic in real-time with minimal performance impact. Instead of relying on traditional methods like tcpdump, which often involves significant overhead, eBPF allows for efficient filtering and inspection of packets directly within the kernel. This efficiency is especially beneficial when analyzing high-volume network traffic.
Examining TCP/IP Headers with eBPF: A Practical Approach
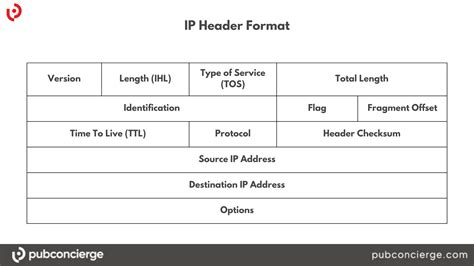
eBPF provides access to various kernel data structures, including network packets. By leveraging this access, we can write programs that inspect specific fields within TCP/IP headers. For instance, we can track source and destination IP addresses, ports, packet sizes, and various TCP flags. These programs can then output this information to a user-space application for analysis.
How to use eBPF for TCP/IP header examination?
While the specifics depend on the chosen eBPF tooling (BCC, bpftrace, etc.), the general process involves:
-
Defining the eBPF program: This program acts as a filter, specifying which packets to examine based on criteria like IP addresses, ports, or protocols. It also defines the specific header fields to extract.
-
Attaching the program to a kernel hook: This involves linking the program to a specific kernel event, such as the
skb_v4_rcvorskb_v6_rcvfor IPv4 and IPv6 respectively. These events trigger every time a packet is received. -
Processing the data: The eBPF program extracts the desired data from the packet header and sends it to a user-space application.
-
Analyzing the results: The user-space application receives and processes the data extracted from the eBPF program, often presenting it in a human-readable format or feeding it to further analysis tools.
What Information Can We Extract from TCP/IP Headers using eBPF?
The possibilities are extensive, allowing for detailed network traffic analysis. Here are some examples:
-
Source and Destination IP Addresses and Ports: Essential for identifying communication partners and tracking network flows.
-
Protocol Type: Determines whether the packet is TCP, UDP, ICMP, or other protocols.
-
TCP Flags: Provides insights into the state of the TCP connection (SYN, ACK, FIN, RST, etc.), helping to identify connection establishment, termination, or errors.
-
Packet Length: Useful for identifying unusually large or small packets that might indicate anomalies.
-
Time to Live (TTL): Helps track packet hops and potentially identify routing issues.
-
Identification (ID) and Fragmentation Offset: For fragmented packets, allows reconstruction of the original packet.
Frequently Asked Questions (FAQ)
What are the advantages of using eBPF over traditional network monitoring tools?
eBPF offers significantly lower overhead compared to traditional tools like tcpdump, making it suitable for high-volume network environments. It's also highly flexible, allowing customization of the data collected.
What are some examples of use cases for eBPF-based TCP/IP header examination?
eBPF can be used for security monitoring (detecting malicious traffic), network performance troubleshooting (identifying bottlenecks), and application performance analysis (monitoring network communication between services).
What are some popular eBPF tools for network traffic analysis?
Popular tools include BCC (BPF Compiler Collection), bpftrace, and some specialized tools built on top of eBPF for specific use cases.
Is eBPF only suitable for Linux systems?
While eBPF is primarily associated with the Linux kernel, similar technologies are emerging for other operating systems, aiming to provide similar functionality.
What are the limitations of using eBPF for network traffic analysis?
eBPF's capabilities are still evolving. Complex analysis might require sophisticated eBPF programs, and the available kernel hooks might not always offer access to all desired data points.
Conclusion
eBPF offers a powerful and efficient way to decipher network traffic by examining TCP/IP headers. Its low overhead, flexibility, and real-time capabilities make it a valuable tool for a range of tasks, from troubleshooting network issues to advanced security monitoring. By understanding the fundamentals and leveraging available tools, you can unlock a deep level of network visibility and gain crucial insights into your network's behavior.